With the spread of COVID-19, many organizations have adopted work-from–home policies, and more people than ever are using online conferencing tools. Zoom, a platform known for its simplicity and reliability, is the platform that has gained the most popularity in recent weeks. As of the beginning of April 2020, the company’s shares have risen more than 200% since the start of the year, even as the S&P 500 has dropped about 20%. Meanwhile, Zoom’s engineering operations team has been adding servers and other equipment at each of the company’s 17 data center locations to accommodate its fast-growing user base.
While convenient and easy to use, however, video conference applications such as Zoom still pose risks for users, including the possibility of eavesdropping, data theft, privacy loss, harassment, and more. In this article, we cover everything you need to know about cybersecurity and privacy in Zoom.
1. Mac Zoom Client Vulnerability
In July 2019, a vulnerability was discovered in Zoom’s Mac desktop client: Malicious websites had the ability to turn on a Mac’s webcam without the user’s knowledge.
This vulnerability stems from how Zoom allows users to start or join a meeting simply by clicking a web link, which creates a local web server that runs on the user’s machine. While this is convenient for users, it also enables meetings with video and audio to be launched without additional user authorization. Thus, while this sign-in method might be user-friendly, it’s not security-friendly, since it allows attackers to start a meeting and turn on a computer’s camera without the computer’s user authorization.
You can protect yourself from this vulnerability by disabling Zoom’s ability to turn on your webcam when joining a meeting, as shown below.
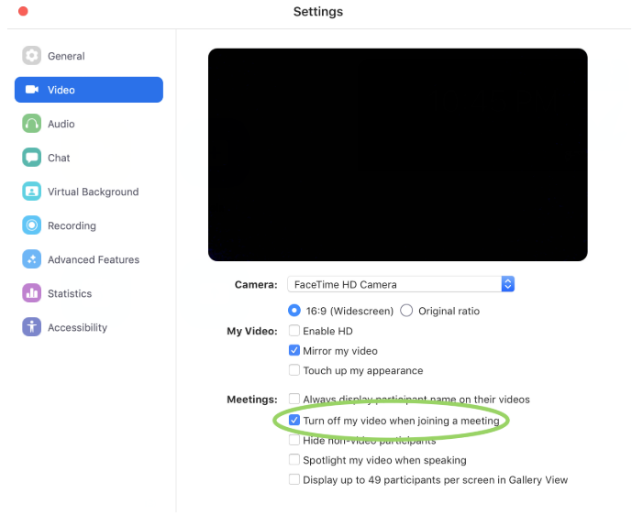
2. Zoom Meeting ID Vulnerability
In January this year, researchers found that it’s possible to exploit the way Zoom generates URLs for virtual conference rooms to eavesdrop on meetings. By using automated tools to generate random meeting room IDs, researchers found during tests that they could generate links to actual Zoom meetings without password protection 4% of the time.
Zoom meeting IDs are composed of 9, 10, or 11 digits. However, if you don’t enable the “Require Meeting Password” option or enable Zoom’s Waiting Room, which allows manual participant admission, these 9, 10, or 11 digits—which hackers can discover fairly easily—are the only thing stopping unauthorized persons from connecting to your meeting.
You can protect yourself from this vulnerability by ensuring you have the latest version of Zoom.
In late March and early April, three new Zoom vulnerabilities were discovered. These are not considered as serious as earlier vulnerabilities since they require more work to execute: Some of the attack vectors require hackers to access a victim’s computer, while another employs social engineering to trick users into interacting with bad actors. Those impacted by these vulnerabilities, however, can still suffer from data theft and abuse.
At the time this article was written, Zoom has not yet taken action to mitigate these vulnerabilities. As Zoom usage increases, we are likely to see more hackers and security researchers trying to find and exploit its vulnerabilities.

3. Privacy
Security flaws such as these are bugs that are occasionally discovered. The best way to protect yourself from them is to keep your software updated and follow the manufacturer’s security guidelines.
First, however, you should be aware of inherent privacy vulnerabilities. There are three main privacy issues in Zoom that you should look out for:
1. Zoom knows if you are paying attention to the call.
Whenever you host a call, you have the option to activate Zoom’s attendee attention tracking feature. This feature alerts the call’s host anytime someone on the call “does not have Zoom Desktop Client or Mobile App in focus for more than 30 seconds.” In other words, if you are on a Zoom call and you click away from Zoom, the host of the call will be notified after 30 seconds, regardless of whether you minimized Zoom to take notes, check your email, or respond to a question on another app. This feature only works if someone on the call is sharing their screen.
2. Zoom collects and shares data.
According to the company’s privacy policy, Zoom collects data on you, including your name, physical address, email address, phone number, job title, and employer. Even if you don’t set up an account with Zoom, it will collect and keep data on the type of device you are using and your IP address. It also collects information from your Facebook profile (if you use Facebook to sign in) and any “information you upload, provide, or create while using the service.” Some of this data you enter yourself when signing in (for example, you must provide your email to join a call), but much of it is collected automatically by the Zoom app. In addition, while Zoom asserts they don’t sell personal data to third parties, it does share personal data with third parties for those companies’ “business purposes.” And that may include passing your personal information to Google.
3. Zoom gives hosts significant power
These capabilities include the ability to record meetings and order transcriptions, as well as the responsibility for any meeting data safe, whether it’s stored on a laptop or under a host’s password in Zoom’s cloud.

How can you protect your data?
There are three easy ways to protect your privacy during Zoom calls:
- Use two devices during Zoom calls. If you are attending a Zoom call on your computer, use your phone to check your email or chat with other call attendees. This way, you will not trigger an attention-tracking alert.
- Do not use Facebook to sign in. While this saves time, it’s a poor security practice and dramatically increases the amount of personal data Zoom can access.
- Look for an icon that tells you when a meeting is being recorded by the host. If you feel comfortable doing so, ask your host to turn on the feature that requires participants to provide consent before a recording can begin. If you’re hosting a videoconference, we suggest you use the feature, which is turned off by default.
4. Virtual Events
With many now confined to home, people are increasingly using Zoom to host virtual events. Zoom has published its own tips and recommendations for maintaining security and privacy while managing such events:
- When you share your meeting link on social media or other public forums, that makes your event … extremely public. ANYONE with the link can join your meeting.
- Avoid using your Personal Meeting ID (PMI) to host public events. Your PMI is basically one continuous meeting, and you don’t want unexpected people crashing your personal virtual space after the party’s over.
- Familiarize yourself with Zoom’s settings and features so you understand how to protect your virtual space when you need to. For example, the Waiting Room is an extremely helpful feature that allows hosts to control who comes and goes.
1. Manage screen sharing
The first rule of the Zoom Club: Don’t give up control of your screen.
You do not want random people in your public event to take control of your screen and sharing unwanted content. You can restrict the ability to screen share from the host control bar both before and during the meeting.
2. Manage your participants
Zoom offers a number of options for managing meeting participants:
- Allow only signed-in users to join: If someone tries to join your event but isn’t logged on to Zoom with an email to which the invitation was sent, they will receive the message “This meeting is for authorized attendees only.” This option is useful if you want to control your guest list and invite only those you want to your events, such as colleagues or other students at your school.
- Lock the meeting: It’s always smart to lock your front door, even when you’re inside the house. When you lock a Zoom meeting that’s already started, no new participants can join, even if they have the meeting ID and password (if you have required one).
- Set up your own two-factor authentication: This option lets you generate a random Meeting ID when scheduling your event and require a password to join. You can then share that Meeting ID on Twitter but send the password only to invited participants via DM.
- Remove unwanted or disruptive participants: You also have the option to remove participants from your meeting.
- Put participants on hold: You can also put everyone else on hold, and the attendees’ video and audio connections will be momentarily disabled.
Other options include disabling a participant’s video, muting participants, blocking file transfer through the in-meeting chat, disabling the private chat function, and more.
For more detailed instructions, check the above links as well as this article, then watch the following video.
3. Try the Waiting Room
One of the best ways to use Zoom for public events is to enable the Waiting Room feature. Just as its name suggests, the Waiting Room is a virtual staging area that stops your guests from joining until you’re ready for them. It’s a bit like the velvet rope outside a nightclub, with you as the bouncer carefully monitoring who gets to enter.
Meeting hosts can customize Waiting Room settings for additional control, and you can even personalize the message attendees see upon entering the Waiting Room so they know they’re in the right place. The Waiting Room is an optimal location for posting any rules/guidelines for your event, such as its goals and who it’s intended for.
This video provides additional details.
Summary
Zoom is focused on making something that was formerly complicated, such as video conferencing, extremely simple for users. However, technology almost always involves a trade-off between convenience and security, and it’s common for the very technology that we use to be more productive to put us and our personal information at risk.
Now you know how to protect yourself while using Zoom and how to avoid eavesdropping, data theft, privacy loss, and online harassment. In summary, the most important items to remember about cybersecurity and privacy in Zoom are the following:
- Keep your Zoom software up to date.
- Disable Zoom’s ability to turn on your webcam when joining a meeting.
- Do not use Facebook to sign in.
- When hosting an event, manage your meeting settings and participants.
- When participating in meetings, be aware of whether or not the meeting is being recorded.
- Read the privacy policy and terms of service before using it. If you aren’t satisfied, use an alternative.
Remember, even if you choose not to use Zoom, many of these guidelines also apply to other video conference applications and other digital tools. Stay safe!




