Netflix’s Black Mirror takes us to brilliant alternate realities where advanced technology poses dramatic consequences and blurs ethical lines. While some of these technologies seem futuristic and outlandish, some Black Mirror concepts aren’t a far stretch from today’s technological capabilities.
It’s no secret that advances in tech can come with cyber security complications. Here are some Black Mirror episodes that shed light on huge cyber security threats. The worst part? These scenarios are frighteningly plausible.
Warning, spoilers below.
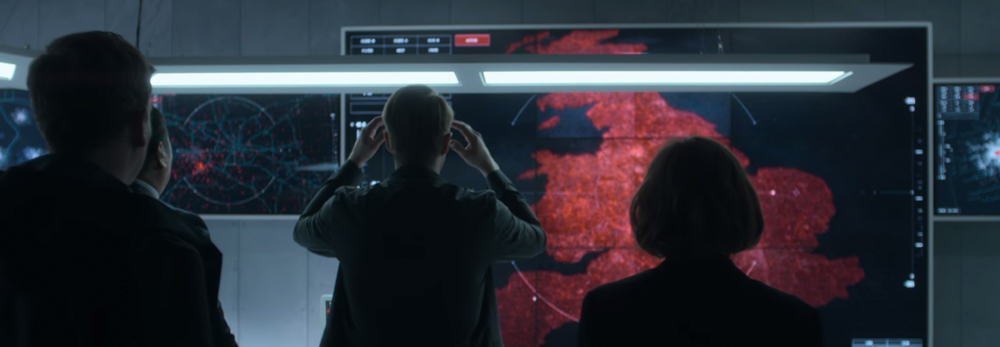
Hated in the Nation
It’s the future, and bees are nearly extinct. To prevent ecological catastrophe, the government funds a project that deploys bee-like drones, or Autonomous Drone Insects (ADIs) to replace the declining bee population. Unbeknownst to the public, the government used the ADIs to spy on the public using facial recognition, under the argument that they can prevent terrorism and crime.
In retaliation against online public shaming and hateful online rhetoric, an extremist hacks the ADI system, simultaneously inciting more online mob mentality with the sole purpose of ultimately using the ADIs to carry out a mass execution of social media users who used the #DeathTo hashtag.

Luckily, we don’t have to worry about frightening big-brother bee-drones in real life, at least not yet, but this episode touches on a lot of larger issues. In the scope of cybersecurity, governments are a hot target for cyber criminals. In our everyday lives, it’s easy to forget that critical infrastructure systems like electrical grids, power plants, and entire transportation systems are being hacked, and these types of attacks are on the rise.
Shut Up and Dance
In this episode, a hacker uses fake anti-malware software to spy on users through their computer webcams, collecting leverage on them, like evidence of an extramarital affair, racist remarks, or illegal activity. The hacker then uses this information to blackmail them into doing elaborate and difficult tasks, and his victims comply out of fear of having their secrets exposed. Even though they complied with every single request, going to great lengths to complete tasks like robbing banks and fighting each other to death, they were each ultimately exposed.
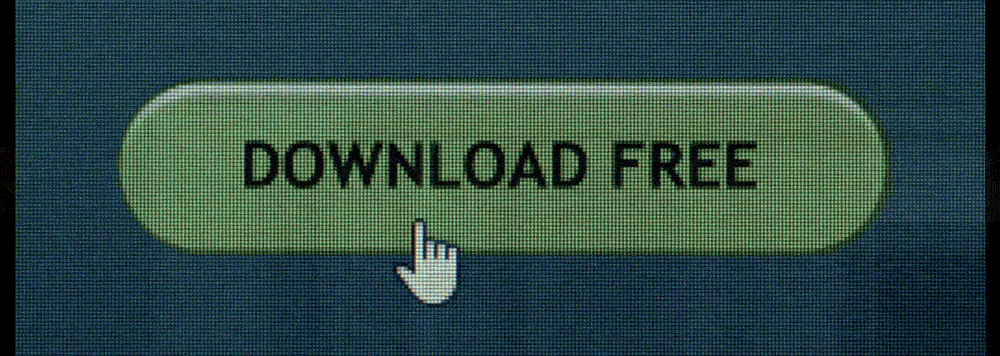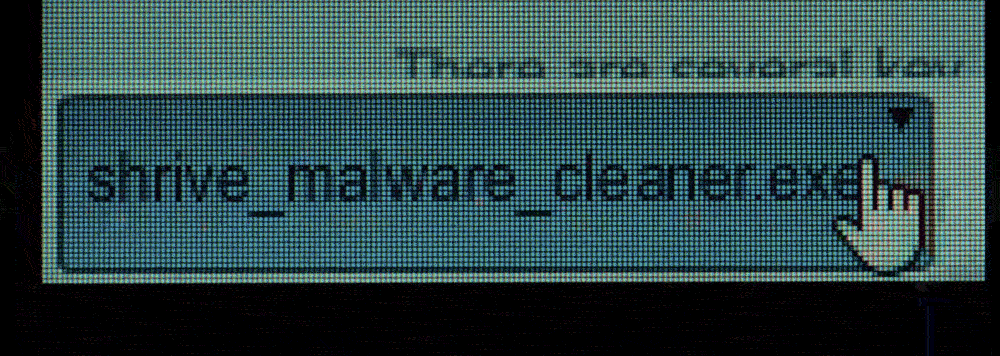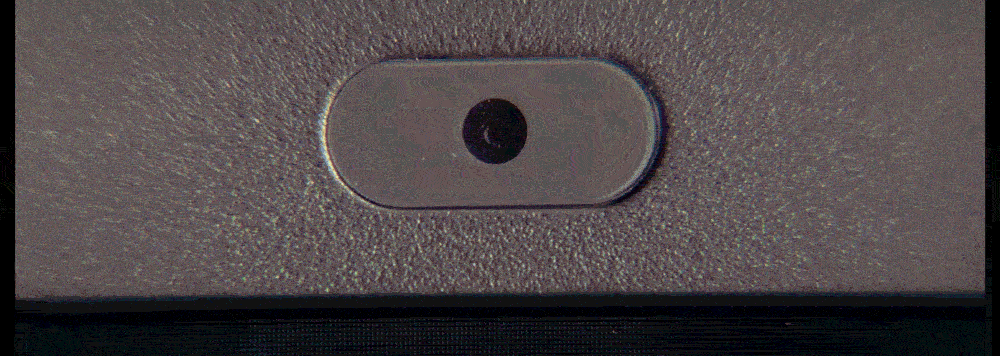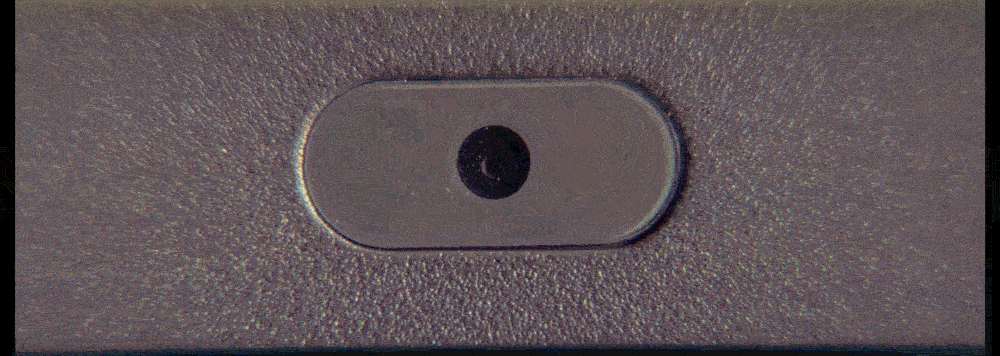
In the real world, one of the biggest motivators for cyber-crime is, of course, money, but other motivators can be for political reasons, revenge, or just for fun. Some readers might remember the infamous Ashley Madison data breach, in which a group of hackers leaked the user database of Ashley Madison, presumably because the site encouraged affairs.
Just like in this Black Mirror episode, complying with the requests of hackers isn’t a good idea. Hackers have extorted large sums of money by carrying out ransomware attacks, in which the user’s files are encrypted until the ransom is paid in exchange for a decrypt key. But it’s not always a good idea to pay the ransom. Not only does it give incentive to the hacker to strike again, but a payment is never a guarantee the files can be retrieved.
Grab our free guide on Ransomware: Everything You Need to Know
Nearly Every other Black Mirror Episode
In standard Black Mirror fashion, other episodes typically include concepts like artificial intelligence, virtual reality, tracking devices, etc. While there’s no cyber hacking happening in most episodes, these days, even a refrigerator can be hacked. Knowing this, it’s hard to watch knowing that some of these technologies are here, present today, and pose huge cyber-threats.

Sure, some Black Mirror concepts seem like they’ll remain entirely fictional, like injecting parental supervision systems into our children, or uploading one’s consciousness onto a device (we see this theme in many episodes, like “Rachel, Jack and Ashley Too” and “White Christmas”), but some Black Mirror technologies already exist, like machine dogs, inspired by real-life military robots, and using Artificial Intelligence to simulate the deceased in episode “Be Right Back,” just as we can in real life.
Breakthroughs in technology are constantly disrupting the cyber landscape, making cyber security more complex. But the biggest risk is believing you can’t become the victim of a cyber-attack. Staying up-to-date with cyber education can go a long way in minimizing risk. Contact us to get started.




