Cyber intelligence refers to the process of gathering, analyzing and interpreting digital information. Not only is cyber intelligence vital to an organization for a strong security posture but has been effective in increasing workplace efficiency and due diligence.
The breadth of information and data stored on the Internet is endless, and new information is constantly generated. Studies show that most people are only accessing 5% of the information they need for work, so understanding how to improve these practices can skyrocket performance and efficiency. In this article, we’ll cover these important tips to improve your output:
1. Searching Better
Using search parameters in your Google search queries such as file type, help to narrow down the results to more targeted information that would have otherwise been buried in irrelevant links. Let’s go through an example:
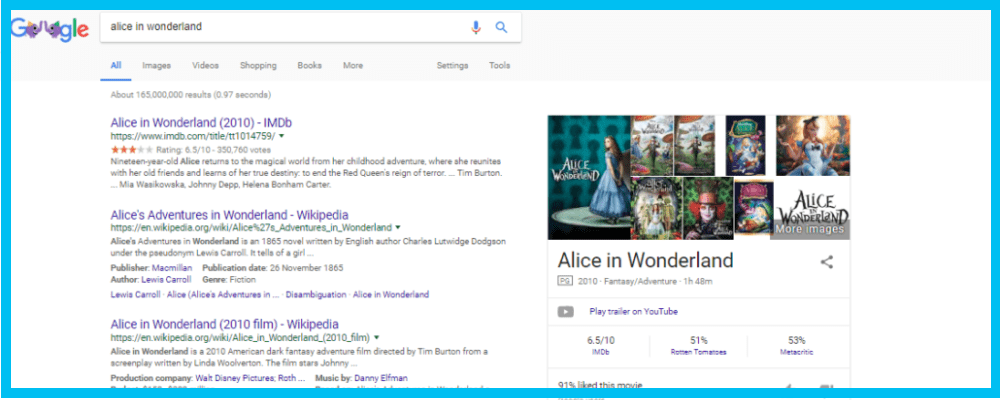
Let’s say we’re looking for a downloadable copy of Alice and Wonderland. By typing in the title, the results may contain the movie’s IMDB page or reviews of the book. The results are at 145,000,000 which are still too broad.
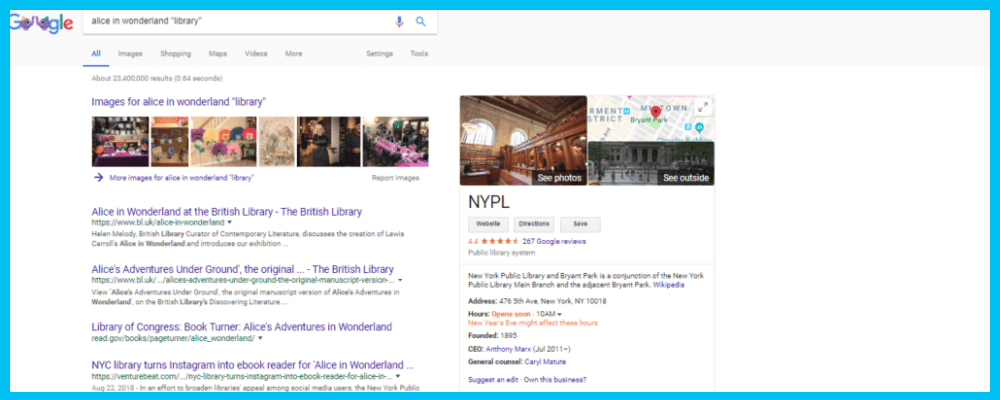
So let’s add the word “library” in quotations, meaning the search results MUST contain that word and we want a copy that is from the library. As you can see there are about 23,400,000 results.
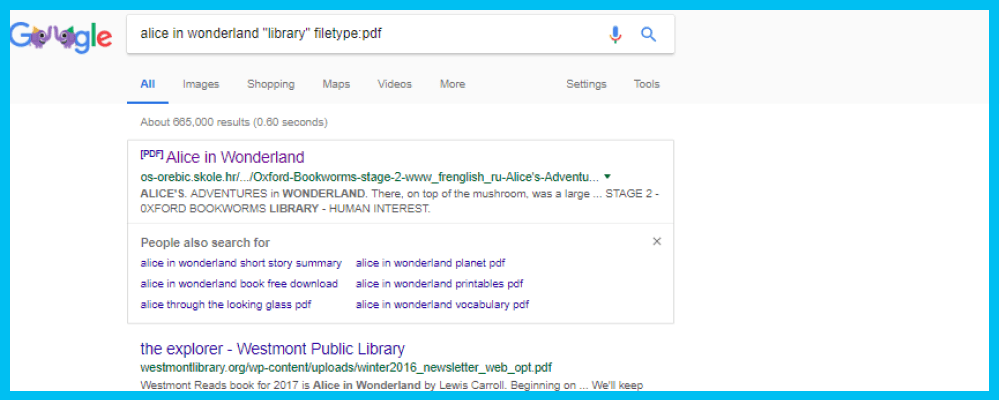
Still, our results could be better, so we add in another parameter that reads filetype: PDF. This narrows the results to only PDF pages of Alice and Wonderland from the library. Now, there are only 665,000 results, reduced from 145 million.
The first link is from the Oxford Bookworm’s Library and is a complete, downloadable version of Alice and Wonderland in PDF form.
2. Accessing Hidden Data
Data is not always easy to find on the web because most of the available resources are visible only to machines. People navigate the web visually, viewing content, clicking on links and downloading files. While humans look for engaging, interactive content, machines require structure, logic, and clarity.
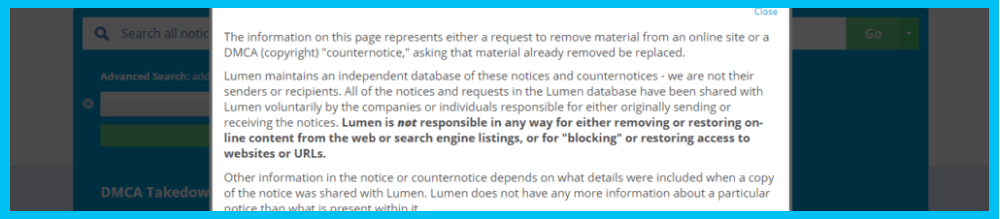
The benefits of hidden include improved quality, relevance, context and breadth of our search. In this example, we’ll be using the tool, Lumen, an online archive that enables users to search for information that was requested to be deleted by an organization or individual from online.
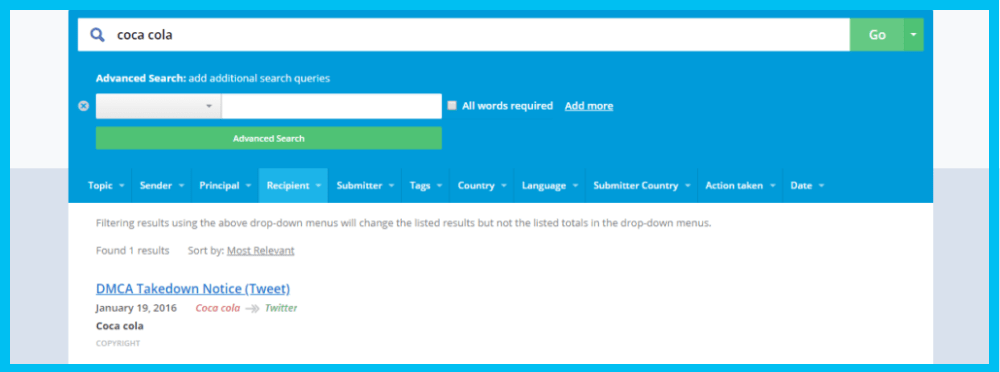
Let’s say we want to find out if the Coca-Cola Company has had a cease and desist notice issued on its behalf.
Similar to the first example, we’ll want to narrow these results using the “advanced search” option. We want to filter down on the recipient, by choosing Twitter.
Here we can see that the subject of the notice is a DMCA takedown notice, meaning Coca-Cola requested that Twitter remove specific content, probably from a Twitter account or a specific tweet because it violates its copyrights.
3. Uncovering Deleted Information
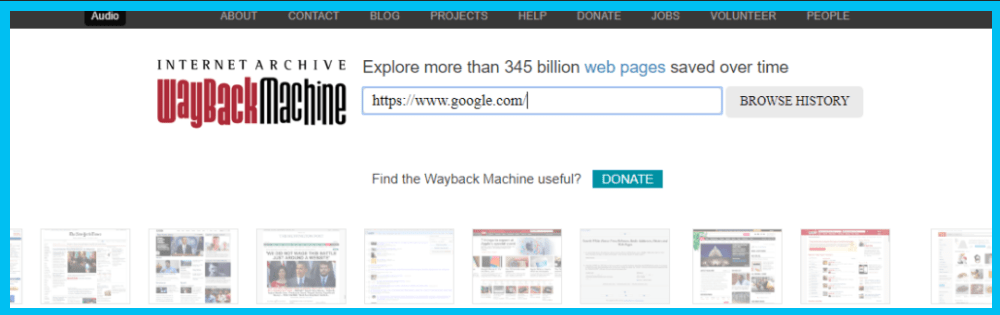
We’ve covered search hacks, hidden data hacks, but what about accessing information that was changed? In this example, we’ll be using the tool Wayback Machine which uncovers deleted data from the Internet, regardless of the reason it was deleted (whether it was outdated, deliberately deleted, etc.), to find and save specific webpages for future use, and for investigating the changes that have been made on a specific webpage. This type of tool is especially beneficial to those in law enforcement and legal careers.
Let’s check Google.
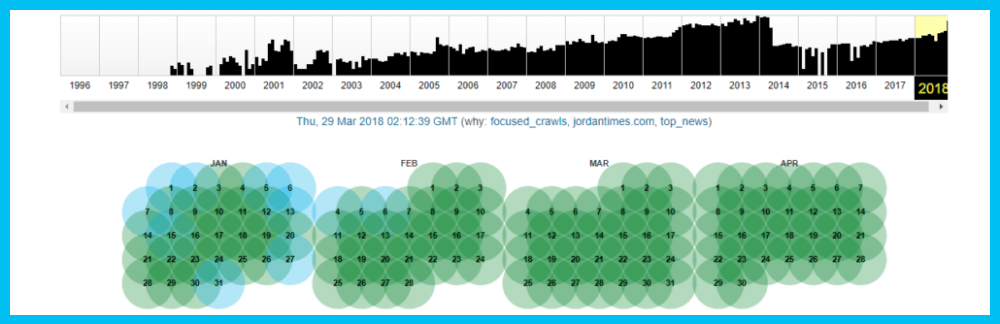
The first thing we see is a summary of data collected on the website over time. Then, you can choose the year you desire and the calendar will open up.
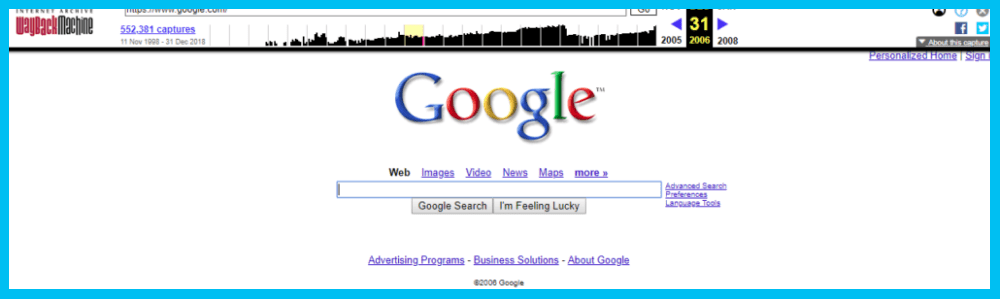
Let’s choose December 31st, 2006. Choosing a specific time may not make much of a difference but you do have that option. Here is a preview of Google from that exact date:
As you’ve learned, in order to access hidden information, you don’t need a secret password, an invitation from an inside member or hacking tools. All you need is a computer and an internet connection. As long as the proper tools and methods are used, the data is only seconds away from anyone who can access the regular web.
These tools along with proper cyber intelligence training can help your employees successfully navigate the Web to find the right information and data, in order to avoid crucial mistakes, and gain a competitive edge. For more information on our cyber intelligence resources and services, please contact us here.